How to Use Tor Browser
Let’s see how to use Tor Browser, a perfect anonymous browser

Date: 2014-07-30 08:12:41
By:
In order to follow this guide you will need to download Tor Browser. Please click the green button below.
When we use this browser for the first time it will need a slight setting up, depending on what we are going to use it for, let's learn how to use it. In this window we see below we can choose to connect to a Tor Network right away or to any other proxy we want. Anyway, Tor Network as it is assures anonymity, but if we want to use another proxy, let’s see how to do it.
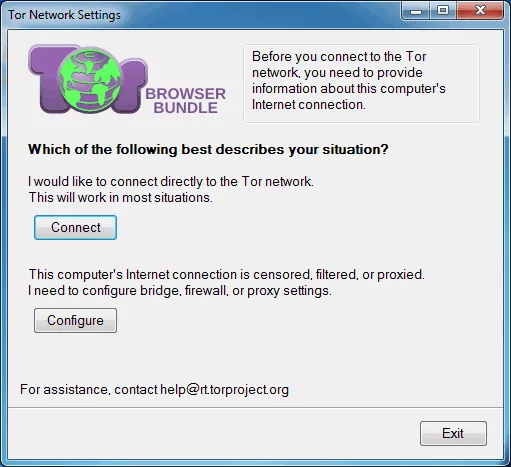
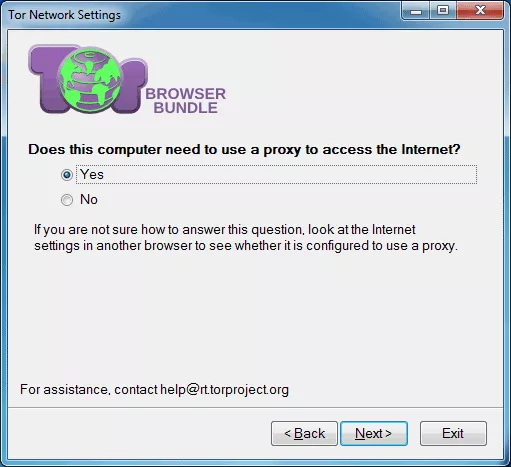
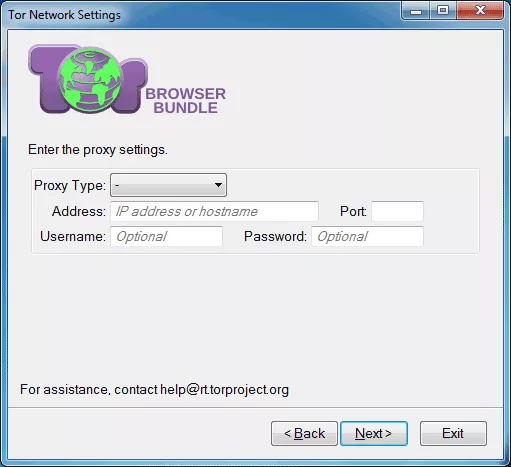
If your network requires a separate proxy address for Internet connection, Tor Browser gives you an option to do so. We just need to choose “Yes” and in the next step you will be able to introduce all the necessary data for network connection. For more security and anonymity of the network it is recommended to use safe and trusted proxy, or paid proxy. Anyway, not any proxy may be valid, so you need to know to choose right before using any.
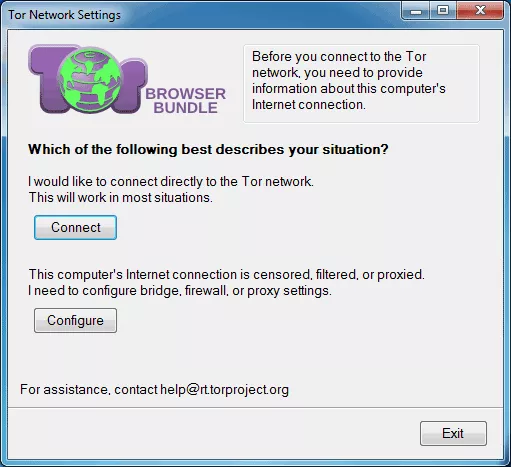
Now, going a few steps back, we will choose the option of connecting to Tor proper network, and let’s see the easy it is to use it. We simply need to click on “Connect” and we will see a window saying “Connecting to the Tor network”. When the process is finished, Tor Browser will auto restart and we will be able to start using it and see its main features.
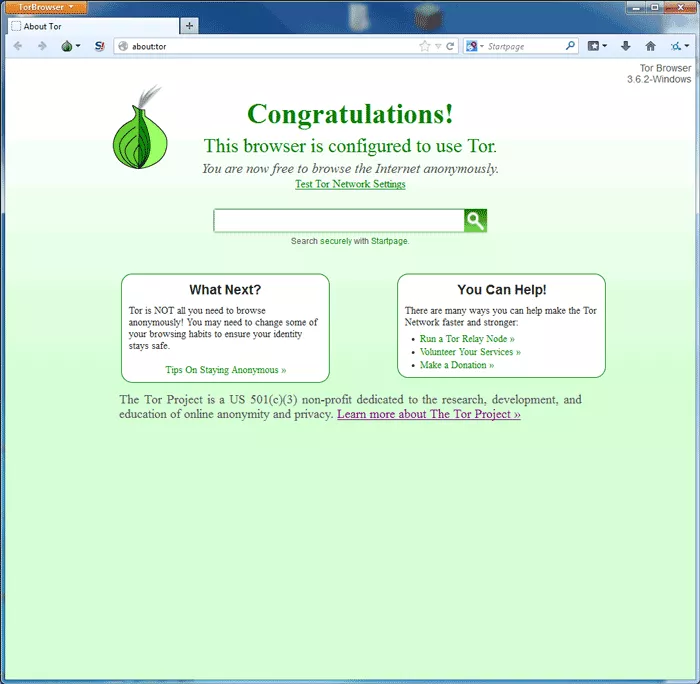
Its interface is very similar to Firefox, in fact, both browsers use the same engine. Now we can see that we “are now free to browse the Internet anonymously”. And it is really so.
Let’s now see some privacy options of this browser. As we can see, all is configured perfectly for us not to have any unnecessary worries about our privacy.
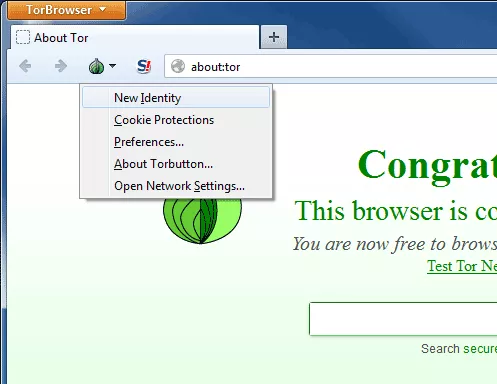
A very useful tool available with Tor Browser download is creating new identity. Even though the browser doesn’t track your IP or search history, it’s recommended to refresh the IP address from time to time. When we choose this option, the browser restarts in a matter of seconds and we will already have our new Internet “identity”.
How to Install Tor Browser
Start using Tor Browser right now by simply following this intuitive installation guide
So, the last thing we did was to download Tor Browser files, and now we need to install it. Let’s double click over the file. We will see this small window where we will have to choose installation
Security Essentials guide: Protect your Internet privacy and discover other tools to keep yourself safe
If you’ve read Rocky Bytes in the past, you know we take internet privacy and security very seriously. We’ve discussed the topics of anti-censorship and tracking tools at length and have taken great strides into having the best software available for you to keep yourself safe from the dangers ...
Psiphon alternatives: more Censorship Circumvention Tools
If you’ve read our articles in the past, then you know we’re big fans of censorship circumvention tools such as Psiphon, Tor Browser, Ultrasurf and Hotspot Shield. But with the articles in the past few months, we’ve written all there is to
Psiphon fixes mobile data-plan bug and prove they play by the rules!
Psiphon is one of the best internet censorship circumvention tools in the world and here at Rocky Bytes, we’ve spoken at length about its history helping people around the world get through unjust censorship and outright blockage of internet services by less than agreeable governments. Censorship ...










